- Why Edgenexus?
- Try
- Products
- Solutions
- Applications
- Resources
COMPARE
READ
WATCH
SEE
Alliances and Partners
- Support
ZAP Attack Proxy

What is it?
The ZAP web application attack tool is used to run simulated application layer attacks against a web application. Please ensure you have permission from the application owner before you use this tool.
Whilst we recommend using the Chrome browser for the management access to the appliances you will want to use another browser to generate the test traffic and I’d recommend Firefox for this purpose.
ZAP is started by connecting your management (Chrome) browser to :8080/zap/.
When you do this you will first see the first ZAP webswing initializing screen. The attack proxy is running as an application on the jetNEXUS load balancing host, it can be accessed with the credentials provided by Azure and the URL below:
This will change to the next ZAP startup.
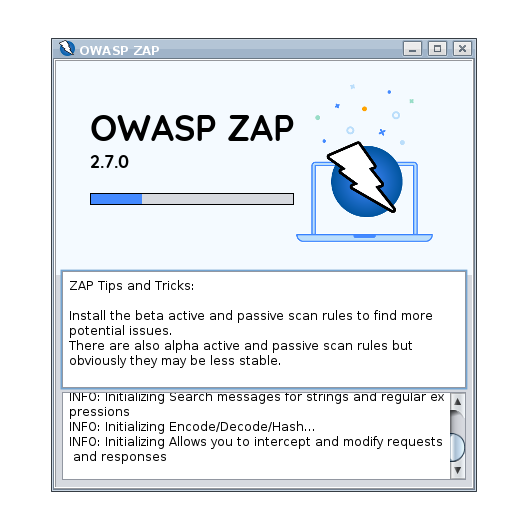
And then you have the option to choose whether you want to persist the session, so it can be loaded again afterwards. For the test drive this probably isn’t required.
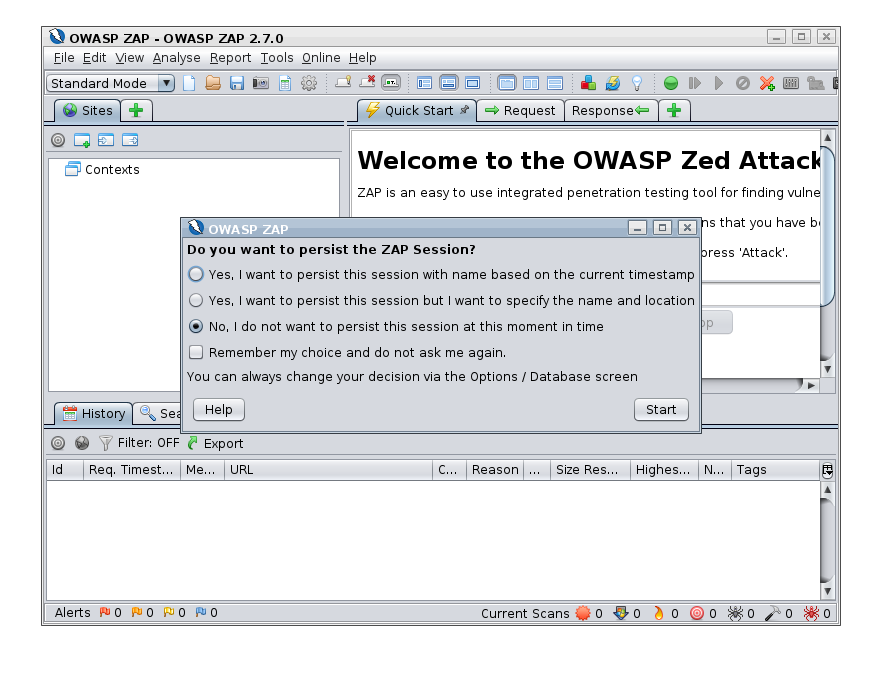
Once this is complete ZAP will be running and the LED on the 8090 IP service will change from Red to Green showing the TCP health check is passing as port :8090 is now open.
- We now need to configure the browser to use a proxy.
You can now configure your Firefox web traffic browser to use the ZAP Public IP address and port :8090 as the Network Proxy.
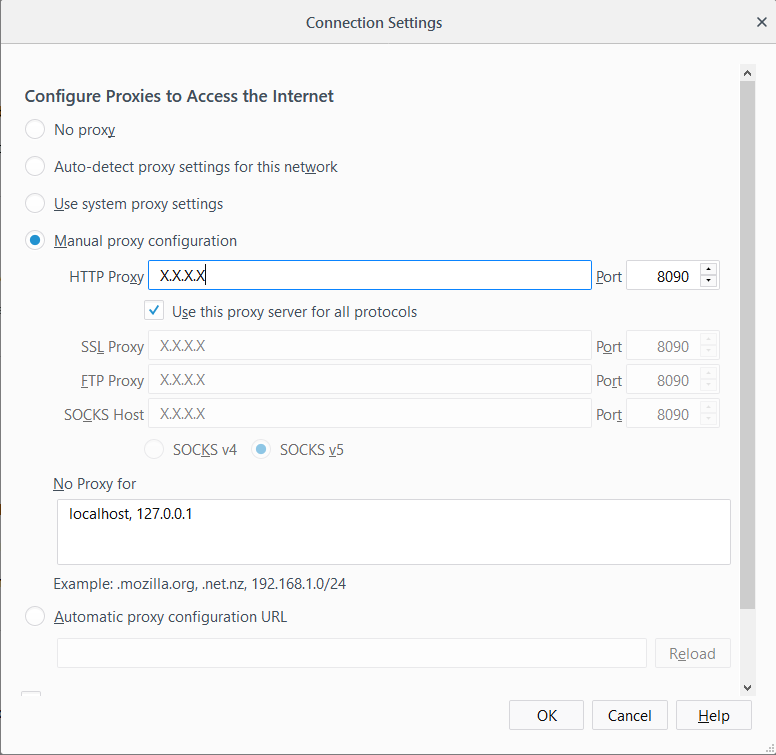
Using ZAP
There are a few steps to follow to set up ZAP to first spider the application and then perform an attack. I would refer you to the several online resources for details on how to set this up rather than regurgitate the information here.
Where it refers to setting your browser proxy to localhost, you have already performed the necessary configuration steps above.
Viewing the Results
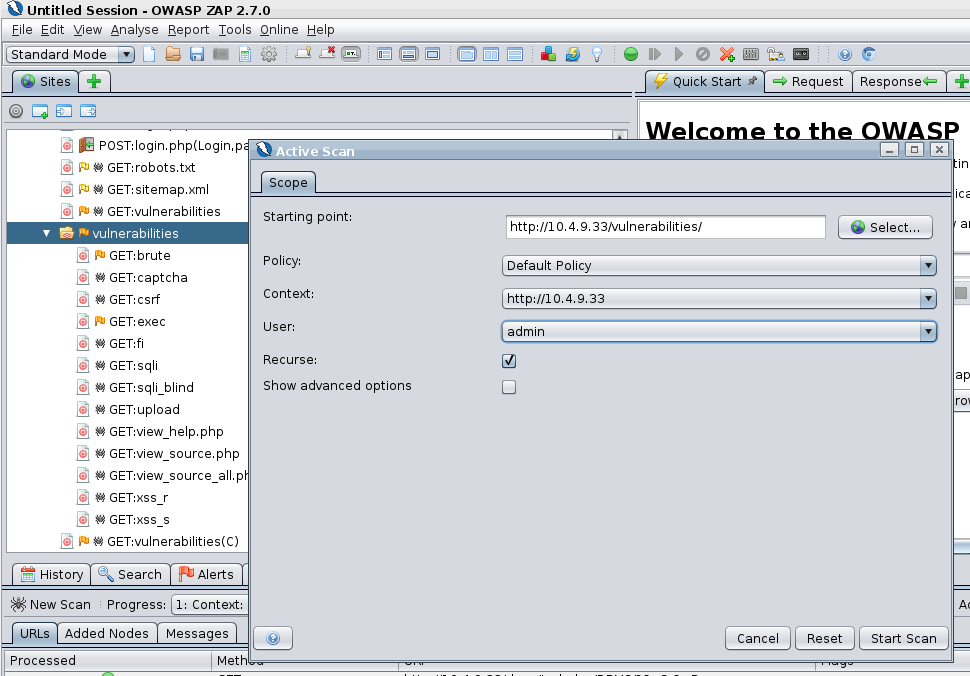
When you have performed the attack you should be able to view the results in the ZAP Proxy
- Here you can see the vulnerabilities tree that was spidered and then attacked as the admin user.
Damn Vulnerable Web App (DVWA)
A configurable Target web server that can be used to test your WAF and Attack tool
ZAP Web Application Attack Tool
Web Application Attack Tool is a vulnerability scanner based on OWASP ZAP
We would love to hear from you
- People say we are knowledgeable and friendly but you can be the judge of that.
Don’t take our word for it – take a free trial
Hardware, software or even your own online image complete with a full test environment.
Just let us know what you need here
APP STORE

