The Game Changer: Why Application Delivery Controllers are the Secret Sauce for High-Traffic Websites
In today’s digital landscape, the success of your online business depends on your ability to provide a seamless, lightning-fast, and secure user experience. As your website’s traffic grows, so does the demand for resources and the complexity of managing it. Application Delivery Controllers (ADCs) have emerged as an essential tool for high-traffic websites that crave efficiency, scalability, and security.
What are Application Delivery Controllers (ADCs)?
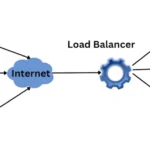
Before we delve into the benefits of ADCs, let’s first understand what they are and how they work. ADCs are advanced networking devices that manage and optimise the delivery of web-based applications to end users. They provide many services, such as load balancing, SSL offloading, traffic management, and security features, to ensure the seamless delivery of applications to users.
The rise of high-traffic websites
With the exponential growth of the internet, businesses have realised the power of a robust online presence. High-traffic websites are becoming the norm, so the need for solutions that can handle this level of traffic has never been more critical. This surge in demand has led to the evolution of ADCs as the go-to solution for managing and optimising high-traffic websites.
ADCs and SSL handling
Load balancing is a critical feature of ADCs that evenly distribute network traffic across multiple servers to ensure no single server is overwhelmed. This allows for improved application performance, reduced latency, and increased availability, all essential for high-traffic websites. ADCs use various algorithms and techniques to intelligently route user requests to the most appropriate server, considering server load, proximity, and response times.
SSL Passthrough
SSL Passthrough is a vital technique utilised in Application Delivery Controllers (ADCs) for managing secure network traffic. It allows client-to-server Secure Sockets Layer (SSL) or Transport Layer Security (TLS) connections to be transmitted directly through the ADC to the server without being decrypted and re-encrypted. This process ensures that the ADC does not bear the processing load of decrypting and re-encrypting the SSL/TLS traffic, thereby improving performance and reducing latency. Moreover, it ensures the traffic remains encrypted end-to-end, enhancing sensitive data’s security and privacy. However, because the traffic remains encrypted, the ADC cannot inspect or manipulate the data at the application layer, limiting some of the more advanced Layer 7 functions such as traffic shaping, content switching, and intrusion prevention. Thus, while SSL passthrough offers benefits in terms of performance and security, its usage is a trade-off that needs careful consideration based on specific application needs and security requirements.
SSL Offloading
Secure Sockets Layer (SSL) offloading is aimed at optimising the performance of web servers. This process involves transferring the CPU-intensive task of encrypting and decrypting SSL traffic from the web servers to the ADC. As SSL/TLS encryption has become a standard practice to ensure secure communication over the internet, the computational load on servers has significantly increased. SSL offloading relieves this burden from the servers, enabling them to dedicate more resources to their primary function of serving application content, thus improving overall performance and user experience.
SSL offloading also provides benefits beyond performance enhancement. Centralising the SSL function on the ADC simplifies certificate management, as all certificates can be managed in one place rather than on each server. Moreover, since ADCs are designed to handle SSL encryption and decryption, they often perform these tasks more efficiently than general-purpose servers. Furthermore, ADCs are equipped for SSL processing, enhancing their efficiency. This ability to offload, centralise, and accelerate SSL processing is a significant advantage of using ADCs in modern web application environments. It ensures that secure communication is not at the cost of application performance or server efficiency.
SSL Re-Encryption
Secure Sockets Layer (SSL) encryption is a widely used protocol for securing data transmission over the internet. In today’s digital landscape, SSL encryption is crucial for protecting sensitive information and ensuring the privacy and security of online transactions. Regarding load balancing, SSL re-encryption is essential in maintaining secure communication between clients and servers.
Understanding SSL Re-encryption
SSL re-encryption decrypts and then re-encrypts SSL traffic as it passes through a load balancer. This process enables the load balancer to inspect and modify the traffic, facilitating various functions such as traffic management, content-based routing, and security features. SSL re-encryption is particularly useful when implementing a secure environment where client-to-load balancer and load-balancer-to-server communications must be encrypted.
The SSL Re-encryption Process
During SSL re-encryption, the load balancer decrypts the incoming encrypted traffic from the client. This allows the load balancer to access the unencrypted data and make intelligent decisions based on the content. The load balancer then forwards the traffic to the appropriate server. Still, before doing so, it re-encrypts the data to ensure the communication between the load balancer and the server remains secure.
Benefits of SSL Re-encryption
- Enhanced Security: By re-encrypting the SSL traffic, load balancers maintain a secure communication channel between clients and servers, reducing the risk of data breaches and man-in-the-middle attacks.
- Improved Visibility: SSL re-encryption allows the load balancer access to unencrypted data, enabling it to make informed decisions based on traffic content. This visibility is essential for efficient load distribution, content-based routing, and the implementation of security policies.
- Compliance Requirements: SSL re-encryption helps organisations meet regulatory and industry-specific compliance requirements, which often mandate that data be encrypted both in transit and at rest.
- Centralized Management: Load balancers with SSL re-encryption capabilities enable organisations to manage SSL certificates centrally, simplifying certificate management and reducing the risk of misconfigurations or expired certificates.
Persistence
In the context of Application Delivery Controllers (ADCs), persistence is a fundamental traffic management mechanism that ensures all requests from a client are directed to the same backend server during a session. This feature is critical for maintaining session data consistency, particularly in environments where user interactions involve multiple requests and responses, such as e-commerce or web applications.
Several persistence methods are used in ADCs, each with its own advantages and applicable use cases:
- Source IP Persistence: This method directs traffic based on the client’s source IP address. It’s simple and effective, but it may not work optimally in cases where multiple users share the same IP, such as behind a NAT device. It’s ideal for environments where each IP corresponds to a single user or client.
- HTTP Cookie Persistence: A cookie is used to identify the client, and the ADC directs traffic based on this identifier. This method is highly reliable as it’s independent of IP address and allows for accurate session persistence, even if a user’s IP changes during a session. It’s ideal for web applications that support and use HTTP cookies.
- SSL Session ID Persistence: This method uses the SSL or TLS session ID for maintaining persistence. It’s ideal for encrypted HTTPS traffic where the application or the ADC cannot inject a cookie. This method is particularly useful in secure applications where encryption is mandatory.
- URL Parameter Persistence: In this method, the ADC extracts a specific parameter from the URL to identify the session. This method is application-specific and requires the application to include a unique identifier in the URL. It’s beneficial in situations where cookies are not supported or disabled.
- Custom Server ID Persistence: This advanced method allows the ADC to insert a custom server ID into the HTTP header or cookie, directly mapping the client and server. This method offers the highest level of control and is ideal for complex application environments.
These persistence methods offer varying advantages depending on the specifics of the application environment. Choosing the right method can significantly enhance the consistency and performance of application delivery, improving the overall user experience.
Layer 7 Real Server Monitors
One critical aspect of ADC functionality is using real server monitors, specifically Layer 7 monitors.
Layer 7 Monitoring: A Deep Dive into Application Health
Real server monitors are vital components of ADCs, responsible for checking the health and availability of backend servers. They operate at different OSI model layers, with Layer 7 monitors focusing on the application layer. Layer 7 real server monitors stand out from lower-layer monitoring options by providing in-depth analysis and insights into application performance.
Rather than merely checking for server availability or response times, Layer 7 monitors examine the application’s content and responses. They can parse HTTP/HTTPS traffic, analyse XML and JSON payloads, and execute custom scripts to interact with the application. This deep understanding of the application’s behaviour enables Layer 7 monitors to detect issues that may be invisible to lower-layer monitoring approaches.
Importance of Layer 7 Real Server Monitors
Granular Application Health Checks
Layer 7 real server monitors allow for granular health checks of the application itself. They can execute specific requests or transactions to verify that the application functions correctly. This level of detail helps administrators identify and resolve issues quickly, minimising downtime and maintaining a high quality of service for end-users.
Enhanced Load Balancing Decisions
By providing a thorough understanding of application performance, Layer 7 real server monitors enable more informed load-balancing decisions. ADCs can distribute traffic based on application-specific criteria, ensuring optimal performance and resource utilisation. This intelligent traffic management can be especially beneficial in complex, multi-tiered application environments.
Improved Security and Compliance
Layer 7 real server monitors can be configured to examine application traffic for signs of malicious activity, such as SQL injection attacks or cross-site scripting (XSS). Additionally, they can help enforce compliance with industry standards and regulations, such as HIPAA, GDPR, and PCI DSS, by analysing and validating application responses.
Proactive Problem Detection
By continuously monitoring application performance, Layer 7 real server monitors can detect issues before they escalate into significant problems. Early detection enables administrators to address potential concerns proactively, reducing the risk of outages and ensuring a consistent user experience.
Customisation and Flexibility
Layer 7 real server monitors offer extensive customisation options, allowing administrators to tailor monitoring strategies to the specific needs of their applications. Custom scripts and application-specific tests can be employed to create highly targeted and effective monitoring solutions.
The increased visibility and understanding of application performance offered by Layer 7 real server monitors contribute to a more resilient and reliable application infrastructure, ultimately resulting in a better end-user experience.
Layer 7 Traffic Management
Layer 7 traffic management represents a smart approach to application traffic and goes beyond the basic load balancing and traffic distribution capabilities found at lower layers of the OSI model. By operating at the application layer, Layer 7 traffic management can make intelligent decisions based on the content and context of application requests and responses. This advanced understanding of application traffic allows ADCs to optimise the distribution of traffic, ensuring efficient resource utilisation and a seamless user experience.
Importance of Layer 7 Traffic Management
Content-Based Routing
Layer 7 traffic management enables content-based routing, allowing ADCs to route traffic based on the specifics of the application request. For example, an ADC can examine the requested URL or HTTP header information to determine the most appropriate backend server to handle the request. This level of granularity allows administrators to optimise traffic distribution based on application-specific criteria, such as user location, client device type, or the nature of the request.
Session Persistence
Session persistence, or “sticky sessions,” is a critical feature in many application environments, ensuring that a user’s requests are consistently directed to the same backend server throughout a session. Layer 7 traffic management supports session persistence by examining application-level data, such as cookies or session IDs, to determine the correct backend server for each request. This capability ensures a consistent user experience and helps maintain the integrity of user sessions.
Application Performance Optimization
By intelligently managing application traffic, Layer 7 traffic management can optimise performance across the application infrastructure. ADCs can make real-time decisions based on factors including server load, response time, and application health, ensuring that traffic is directed to the most appropriate backend server. This dynamic approach to traffic management helps maintain optimal performance, even during periods of high demand or unexpected server failures.
Enhanced Security
Layer 7 traffic management can contribute to a more secure application environment by detecting and mitigating potential security threats. For example, ADCs can inspect application traffic for signs of malicious activity, such as Distributed Denial of Service (DDoS) attacks or attempts to exploit application vulnerabilities. By acting as an application-aware firewall, Layer 7 traffic management helps protect sensitive data and maintain the overall security of the application infrastructure.
Support for Modern Application Architectures
As application environments become more complex, with the increasing adoption of microservices and cloud-native architectures, Layer 7 traffic management becomes even more critical. The advanced routing and traffic optimisation capabilities of Layer 7 traffic management enable ADCs to support these complex environments, ensuring efficient and seamless application delivery.
As organisations continue to rely on web services and applications, the importance of Layer 7 traffic management in ADCs will only continue to grow.
Security and Protection
In addition to performance optimisation, ADCs provide a security layer for high-traffic websites. They can detect and mitigate threats such as Distributed Denial of Service (DDoS) attacks, SQL injection, and cross-site scripting (XSS) attacks. By proactively identifying and thwarting security threats, ADCs help protect the application and its users. This is achieved through features like a Web Application Firewall (WAF), intrusion detection and prevention systems (IDPS), and bot management.
Scalability
High-traffic websites need to have the ability to scale their infrastructure quickly and efficiently as traffic levels fluctuate. ADCs enable seamless horizontal and vertical scaling by efficiently managing the addition or removal of servers from the application delivery infrastructure. This flexibility allows businesses to rapidly adapt to changes in demand without compromising performance or user experience.
Real-World ADC Success Stories
ADCs have proven to be invaluable tools for many high-profile, high-traffic websites.
Below, we will explore some real-world ADC success stories, showcasing how these organisations have harnessed the power of ADCs to manage their high-traffic websites effectively.
Amazon
As one of the largest online retailers globally, Amazon handles millions of transactions and customer interactions daily. To ensure top-notch performance and user experience, Amazon relies heavily on ADCs to manage and optimise its web infrastructure. ADCs help Amazon effectively balance the massive amount of traffic, maintain high availability, and secure customer data throughout the shopping experience.
Netflix
Netflix is a global entertainment powerhouse, with millions of subscribers streaming content simultaneously. The seamless delivery of high-quality video content to users worldwide requires robust traffic management, load balancing, and security features. ADCs play a critical role in ensuring that Netflix can provide an unparalleled streaming experience by optimising network traffic and maintaining high availability across its vast server infrastructure.
As one of the world’s most popular social media platforms, Facebook must manage enormous traffic and user data. ADCs are vital in managing this traffic and ensuring the platform remains responsive and secure. With advanced load balancing and traffic management features, ADCs help Facebook deliver a smooth and engaging user experience to its billions of users.
It’s a Wrap!
In today’s digital age, the need for high-performance, secure, and scalable web infrastructures cannot be overstated. As explored in this blog post, Application Delivery Controllers are essential for high-traffic websites, providing invaluable benefits such as load balancing, SSL offloading, traffic management, security, and scalability.
The success stories of industry giants like Amazon, Netflix, and Facebook demonstrate the power of ADCs in managing high-traffic websites effectively. By implementing ADCs in their web infrastructure, businesses can stay ahead of the competition and provide their customers with a seamless, lightning-fast, and secure user experience.
So, if you’re running a high-traffic website or planning to scale your online presence, consider the game-changing potential of Application Delivery Controllers. After all, they might be your website’s secret sauce to thrive in the digital arena.